Chrome accessories have become easier to imitate
Google Chrome privacy tricks
Kurt The Cyberguy explains how to increase safety and privacy through Google Chrome on your devices when browsing the web.
Chrome extensions are incredibly useful, whether you want to prevent ads, or track the best deals or Enhance your browsing experience. It can be downloaded from the Chrome Web store, which works like the Play store but for extensions. However, extensions are easier to imitate and transform into harmful programs compared to applications.
As we just informed, more than 3.2 million victims were through a linked security breach 16 malicious browser extensionsHighlighting how the attackers exploit the tools that seem to be legitimate to spread harmful programs or steal sensitive data.
Now, security researchers have discovered a multi -shape attack that allows harmful Chrome accessories to turn into other browser accessories, including password managers, encryption portfolios and banking applications, to steal sensitive information.
Keep reading to know how this attack works and how to protect yourself from it.
Chrome browser on the smartphone (Cyberguy “Knutsson)
How does a harmful multi -shape attack works
Security researchers in Squarex Laborators I have found a new attack that allows the malicious Chrome extensions to deny that it is legitimate, such as password managers, encryption portfolios and banking applications, to steal sensitive information. This “multi -shape” attack benefits from the Chrome extension system to deceive users while staying under the radar.
The attack begins with the infiltrators apparently loading as if it is an harmless extension of the Chrome Web store. It may even have real features, such as the Acting Marketing Tool, to persuade users to install them and their relationship to their browser.
Once installed, the harmful extension wipe the victim’s browser for other extensions. You can do this in two ways. If he has permission to use the “Chrome.management” applications interface, he holds a list of installed extensions directly. If not, he is injecting software instructions into web pages to verify unique files or resources linked to certain extensions.
If you find a targeted extension, such as 1password, the malicious extension is due to the attacker -controlled server. Then the attacker tells him that the real extension personality is impersonated by disrupting him if permissions allow, change his name and symbol, and display a fake login window that resembles the real thing.
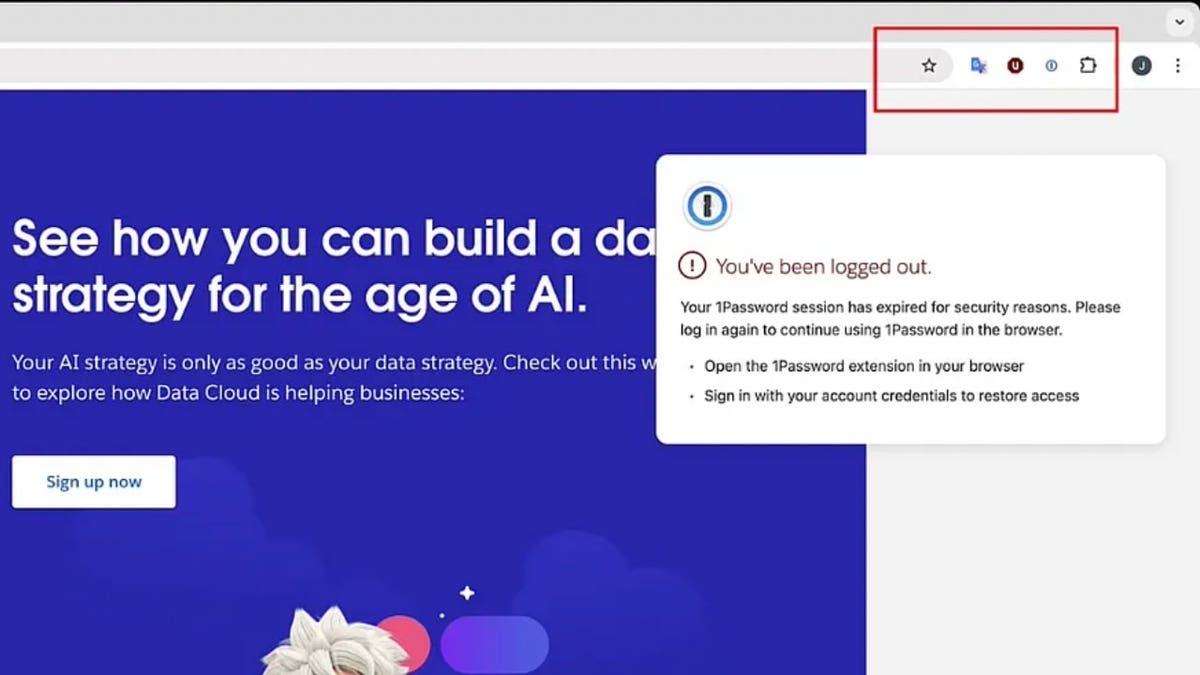
Fake extension page (Squarex)
Hidden costs for free applications: your personal information
Social engineering makes things worse
To steal the user accreditation data, the malignant extension leads to the occurrence of a “fake session” when the victim is trying to log in to the web site. This deceives them to think that they need to re -enter their approval data for the password manager or banking application. When they do, the stolen data is sent directly to the attackers.
After collecting accreditation data, the extension is due to its original shape. It restores the legal extension, which makes everything look normal so that the victim does not suspect anything. This indicates how dangerous the malicious chrome extensions are and why there are stronger security measures to protect users.
We have contacted Google, a Cyberguy spokesman said, “We are able to work the research community and receive the report. We are constantly investing in ways to improve the safety of the Chrome web store, and we take the appropriate action when we learn emerging threats.”
What is artificial intelligence (AI)?

Google Chrome extension on a laptop computer (Cyberguy “Knutsson)
Snements who outperform your identity stealing
5 ways you can protect your personal data
Here are five ways to protect your sensitive information and keep your privacy online.
1. Keep your browser and updated extensions: The outdated software is a gold mine for electronic criminals. Security errors or gaps in old versions can be used from your browser or your extensions to inject harmful software, stealing data or control your system. Updates to correct these security gaps, which makes it the critical defense line. Run your browser automatic updates (for example, Chrome, Firefox, Edge), so you are always running the latest version without thinking about it. See my guide to Maintain update your devices and applications For more information.
2. Install the extensions only from reliable sources: Official browser stores such as the Chrome store are distinguished on the web or additional Firefox additions with rules and survey to arrest bad actors, but they are not perfect. The extensions are likely to hide from random web sites, third -party downloads, malware or spyware. Adhere to the official store of your browser; Do not download extensions from simple links.
Get Fox Business on the Go by clicking here
3. You have a strong antivirus program: The best way to protect yourself from malicious links that prove harmful programs, which may reach your own information, is to install antivirus program on all your devices. This protection can also be alerted to relieving emails and fraud on Ransomwari, and maintaining your personal information and digital assets. Get my choices for the best winners to protect antivirus 2025 for Windows, Mac, Android and iOS devices.
4. Update your passwords: Change passwords for any accounts that may be affected by the extension and the use of unique strong passwords for each account. Think of using the password manager. This can help you create and store strong and unique passwords for all your accounts. Get more details about my country The best password managers reviewed by experts in 2025 here.
5. Invest in personal data removal services: If your personal data is stolen by extension, it is important to act quickly to reduce the risk of identity theft and fraud. Although there is no service to remove all of your data from the Internet, get a great order removal service if you want to monitor and automate the process of removing your information from hundreds of sites continuously over a longer period of time. Check the best data removal choices here.
The massive security defect displays the most popular browsers on Mac
Court Kisa Curt
The harmful extension highlights that Google does not do enough to keep harmful programs from the statute. Security researchers indicated that the Chrome on the web store lacks protection against these types of attacks, such as prohibiting sudden changes on the extension icon or HTML, or at least alert users when these changes occur. The problem is not limited to the Chrome store on the web. The Play Store also hosts harmful applications from time to time, affecting millions of users. Google needs to intensify its safety efforts and put the user’s privacy in the foreground and the center.
Click here to get the Fox News app
Do you trust Google to keep applications and malware from their platforms? Let’s know through our writing in Cyberguy.com/contact.
For more technical advice and security alerts, participated in the free newsletter of Cyberguy Report by going to Cyberguy.com/newsledter.
Ask Court a question or tell us about the stories you want to cover.
Follow Court on his social channels:
Answers to the most amazing Cyberguy questions:
New from Court:
Copyright 2025 Cyberguy.com. All rights reserved.
